

The End Is Nigh for Windows 10:
The Coming Cyber-Apocalypse

If you follow the cyber press, you probably know that support for Windows 10 ends after the updates of October 14, 2025. This is known in cyber circles as End of Life (EoL). Tuesday, October 14, 2025, will be the last "Patch Tuesday" for Windows 10. While the malware definition files for Windows Defender will continue through to 2028, Microsoft hasn't said whether or not updates to Defender antimalware engine will continue past October 14. If there are no more updates to the antimalware engine, improvements in how malware is detected by Windows Defender will not be made past the End of Life date. Also on that date, support for Office version 2016 to 2019 also will end.
Based on working with end users, it is my assumption that those who can upgrade their existing PCs to Windows 11, or purchased newer machines, have already done so. Yet, that leaves many PC users still clinging to Windows 10. The most recent estimate of Windows 10 PCs still in operation was offered by The Register, October 2, 2025. "With just days remaining until Microsoft discontinues free support, Windows 10 still accounts for 40.5 percent of the Windows desktop market." To put this in numbers, it is estimated that between 400 million to 600 million PCs worldwide are still using Windows 10.
The chart below lays out the options for those who do not want to purchase a new Windows 11 PC. There are a few different paths that Consumer users of Windows 10 can follow to continue to receive security patches. It must be noted that, as of now, the offer to continue security updates for Consumers is only for one year. These Eligibility Requirements and Enrollment Paths do not apply to PCs managed by a separate IT department. Note: EEA refers to European Economic Area.
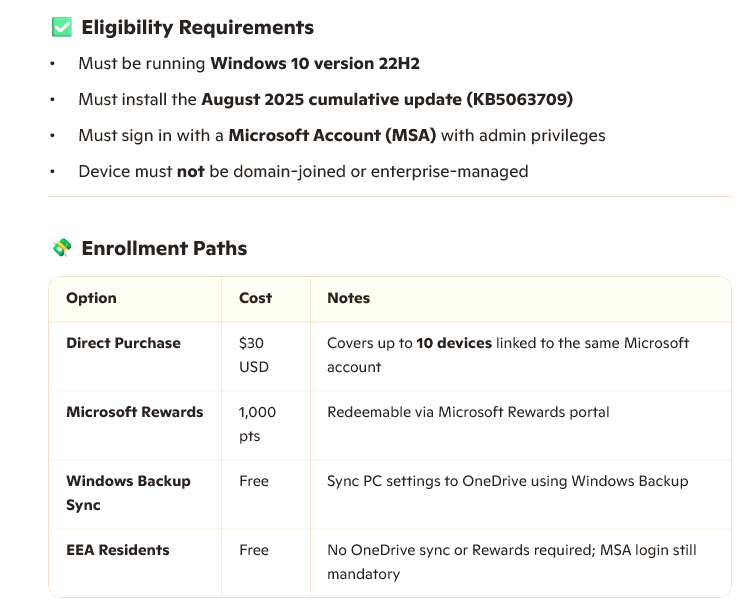
There are several points that must be made concerning what Microsoft calls Windows 10 Extended Security Updates (ESU). The main problem is with the type of individuals who don't update their computers. Some people just plain will not perform updates either because they are not aware of the importance of updating, or they simply do not care. It may sound surprising, but many computer users do not know that they have a Microsoft account. Someone else setup the PC for these folks, and the installer may have never told the actual owner about the MS account. Neither will these users have any idea what version of Windows 10 is installed. And, if that be the case, it is unlikely that they will have installed the required prerequisite August 2025 cumulative update.
Moreover, many people will balk at paying an additional $30 for a product that they already own. For some people today, $30 might not seem like much money, but for many $30 could be food for a day. Moreover, for an employee of the federal government, who might now be facing unemployment, every dollar counts.
One of the most surprising outcomes of Windows 10 EoL is a resurgence in Windows 7. Security upgrades for Windows 7 ended January 2023. It is difficult for me to understand the thinking process that tells someone that since Windows 10 is discontinued October 2025, the solution is to to revert to an operating system that has had no updates of any kind for over almost three years. But there it is.
Nevertheless, the risk of millions of unsecure Internet connected computers represents a threat not just to those who will continue to use their vulnerable PCs, but those unpatched PCs will also be a risk to many other computer users on the Internet. Any malware riddled computer that is connected to the Internet soon becomes a vector for attacks across the network.
The most common words I hear from clients whose computers became infected with some kind of malware is: "But I have antivirus software. Why didn't t it protect me?" Antivirus software can only protect a computer from the strains of malware that the antimalware has been programmed to protect. That is why updating is so important. Updating adds new exploits to what antimalware can protect user from. The greatest threat to all computers and users is from Zero-Day vulnerabilities. CrowdStrike defined Zero Exploits in three ways.
✓ A Zero-Day Vulnerability is
an unknown security vulnerability or software flaw that a threat actor
can target with malicious code.
✓
A Zero-Day Exploit is the technique or tactic a
malicious actor uses to leverage the vulnerability to attack a system.
✓ A Zero-Day Attack occurs when a
hacker releases malware to
exploit the software vulnerability before the software developer has
patched the flaw.
Needless to say, the risks posed by an unpatched PC are formidable. Below is a short list of threats unpatched Windows 10 PCs are liable.
1. Unpatched Vulnerabilities
Once support ends, newly discovered security flaws will remain
unpatched. Attackers often target legacy systems precisely because
they’re no longer maintained.
2.
Limited Antivirus Protection
Microsoft Defender will
continue receiving virus definition updates through October 2028, but
engine updates are not guaranteed. This weakens its ability to detect
novel or fileless threats.
3.
Software & Driver Incompatibility
Third-party apps
and hardware drivers will gradually drop support for Windows 10, leading
to crashes, degraded performance, and data loss.
4.
Increased Malware & Ransomware
Exposure
Unsupported systems are prime targets for
phishing, remote access exploits, and ransomware campaigns — especially in
sectors with compliance mandates.
Among security professionals, it has been well know for some time that computers infected with malware become spam generators. This title of this 2004 article from The Register, "Zombie PCs spew out 80% of spam," states well what all computers users need to know. Malware will harvest a user's contact list, and then send spam out to all those contacts — often exploiting the user's own email address as the sender.
The biggest threat to all Internet users that might arise from unpatched computers are the very real dangers that can come from self-replicating worms. Worms self-replicate across networks without user action. In September 2025, a self-replicating worm that originated from the GitHub code repository infected over 180 other code packages on GitHub. Just recently, October 3, 2025, The Hacker News, reported on a self-replicating worm that originated from the WhatsApp texting application. Once the victim machine was infected, the worm copied itself to the Windows Startup folder. Thus, the malware ran each time the compromised Windows machine started. Most relevant to the discussion here, as reported by Hacker News, is that "there is evidence to suggest that the operators behind the campaign have also used emails to distribute the ZIP files from seemingly legitimate email addresses." Spam email from an infected Windows computer spread the malware far and wide — well, mostly in Brazil.
Of course, all this is well known to cyber criminals. After October 2025, the crooks will prey upon and take advantage of the millions of vulnerable Windows 10 PCs that will not be patched against new threats. So any Windows 10 PC that is still unpatched after October 14, 2025, congratulations — because that PC and its user have volunteered for the malware Hunger Games.

As cyber threats evolve, we need
to evolve as well.
—
Christopher A. Wray
Gerald Reiff