Cookies: The Good, the Bad, and the Ugly
Going on the Defense

Like many things in modern life today, cookies are not inherently good, bad, nor ugly. It depends on the use to which cookies are put. Cloudflare defined cookies as, "small files of information that a web server generates and sends to a web browser." The Cloudflare article linked above is also an excellent and thorough discussion of cookies in general.
Often websites users frequently visit already know the username of users when they first land on that site. That instant ID happens because information about a frequent visitor is stored in a cookie. That might be considered one of the good things cookies can do. One of the bad aspects of cookies is that cookies track users across the Internet. When cookies catalog much of what users do across many different websites, a rather complete profile of an individual user can be created. If that user profile falls into the wrong hands, the victim could be exposed to some kind of identity theft. The ugly side of cookies is that cookies can be exploited to facilitate malware attacks. Cybersecurity News, on April 23, 2025, reported on how stolen cookies were abused to bypass users' credentials for identity authentication purposes, including MFA, to impersonate users, and thereby infiltrating server networks. As the Cybersecurity News put it, "This makes them one of the most valuable targets for infostealers and threat actors."
In a simpler and more innocent time, say before Microsoft Internet Explorer 7 in 2006, cookies were stored as text (.txt) files on the local machine. Since cookies were then stored as txt files, cookie files could be opened and read by any text editor, say like Windows Notepad. Cookies were in a Windows folder labeled "Cookies," and thus were somewhat easier to remove. Since then, cookies are stored in the web browser's cache in a database files that cannot be easily read or deleted by users.
To delete cookies today, certain steps from within the browser Settings must be followed. There are numerous good reasons for deleting cookies. Deleting unwanted cookies will help keep a user's identity private in today's increasingly interconnected world. Another reason for cookie deletion is that doing so will prevent one website from cross-referencing information from a different website. The downside of deleting cookies is any information stored within that cookie, like username and password, will also be deleted. Thus, forcing a user to log back into that website the next time that website is visited. Another downside of deleting cookies is that the next time a user visits the site that had its cookies deleted, that infinitely annoying Cookie Permissions check box will pop back up.
What follows is a tutorial on how to selectively delete cookies from a browser's Settings in either Google Chrome or Microsoft Edge. By selectively deleting cookies, a user can mitigate the downsides of cookie deletion by leaving in place those cookies that are known to the user, and thus websites that are frequently visited.
| In both Google Chrome and Microsoft Edge, the steps and processes discussed herein are very similar. The first step is to get into the Settings menu. In both browsers there is 3 dot control that appears in the top right hand corner of the either browser's screen. When the 3 dot control is clicked a menu of possible tasks appears. Scroll down and click "Settings." | |
| Settings for Edge | Settings for Chrome |
 |
 |
| The easiest way to delete cookies is to simply delete ALL the Cookies. This will, however, log you out of all websites. Except on Chrome, where you will stay logged into your Google account. Before you take this simple step be sure that you have all the usernames and passwords to log back in to all the accounts. The example below is for Edge. I personally do not use Edge for much except reading the MSN news feed and Microsoft Designer AI image generator. So, Edge was a good candidate for demonstrating how to delete all cookies. Click Delete Browsing data highlighted in green above. | |
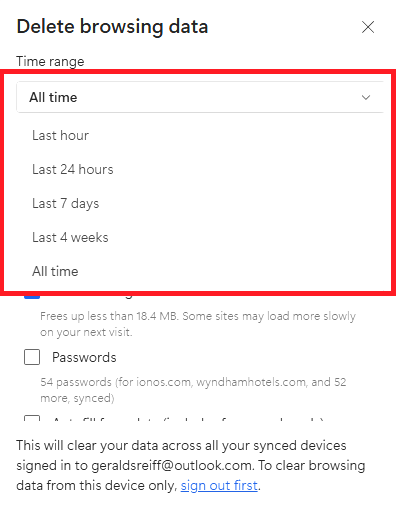
| First, select the time span of data that you want to delete. | Then, select what you want to delete by checking the appropriate box. |
 |
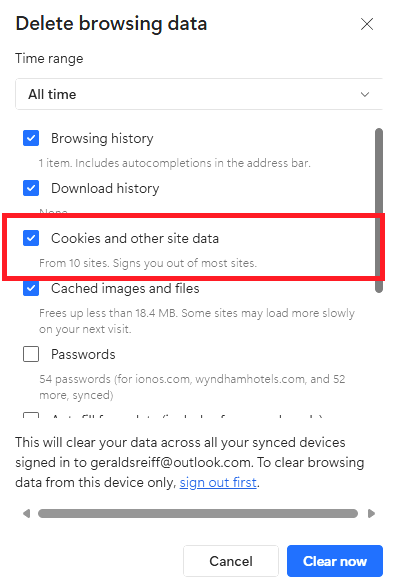 |
| After you delete
all cookies, the next time you go to any of the websites that
require username and passwords, you will be forced to log in
with those credentials once again. Moreover, any lists
that were saved to that website will also be deleted.
And, as mentioned above, the Cookie Permissions Checkbox might
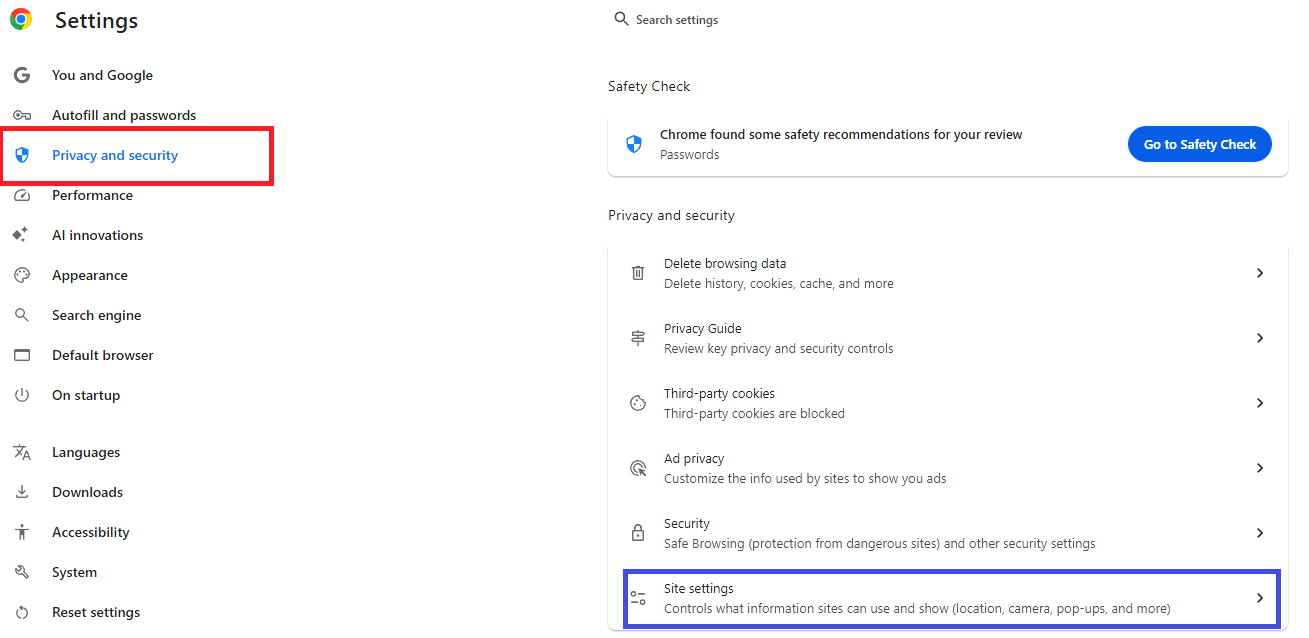
well reappear. On the other hand, if you want to preserve data saved to trusted sites, and only delete data from sites that you have no investment in, you then must delete cookies one website at a time. The upside that you are in control of which websites' cookies retain your data. The downside is this process is very tedious and time consuming. There are no shortcuts here. From within Chrome, click the 3 dot control to open the Chrome menu. Scroll down to the bottom of the menu, and click Settings. When the Settings menu opens, click Privacy and security. Scroll down to the bottom of the menu that is displayed on the right. Click Site settings. |
|
 |
|
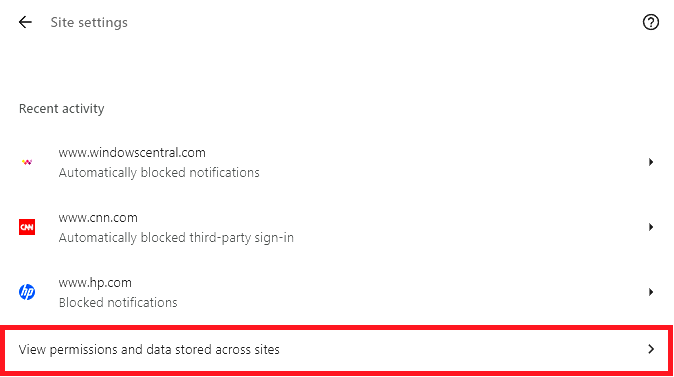
| When Site setting opens, click View permissions and data stored across site. This will open the list of all of the cookies stored within the browser. It can be a bit unnerving when you are confronted with the fact that websites that you have never even visited have left their footprints on your browser | |
 |
|
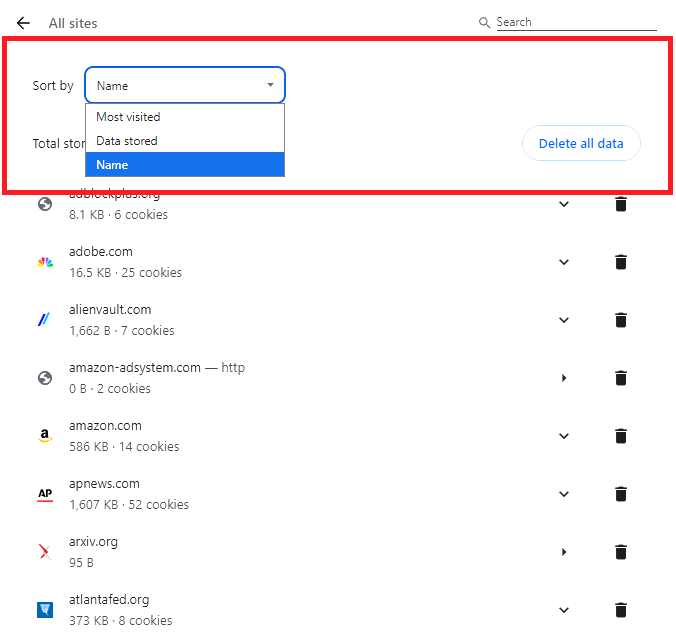
| When view permissions is opened, a long list of websites that have stored data within your browser is displayed. You can sort this list by (a) Most visited, which might help decide if you want to keep this data; (b) Data stored is the total amount of data saved within cookies, and is not the number of cookies; (c) Name sorts alphabetical by domain name. | |
 |
|
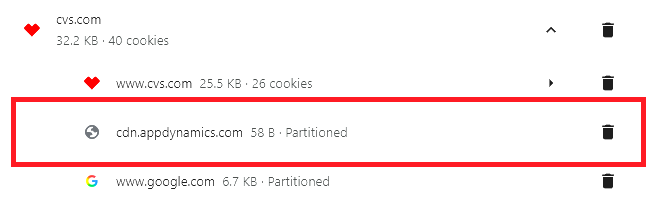
| The trashcan icon will delete the cookie and any other data associated with the cookie. The downward arrow opens up the list of all the types of data associated with that website. This is where things get interesting. Below is an example of data stored by my visiting CVS.com. Notice the domain cdn.appdynamics.com and that that cookie is "Partitioned." According to Wikipedia, AppDynamics "focuses on managing the performance and availability of applications across cloud computing environments, IT infrastructure, network architecture, digital user experience design, application security threat detection, observability, and data centers." [Oh Yeah. Slice me off a piece of that.] Also, take notice of the fact that the cookie for AppDynamics is also Partitioned. According to the Google Gemini AI, Partitioned "refers to a privacy feature that isolates cookies based on the top-level website they are associated with." One benefit of the Partitioning of cookie data is that Partitioning prevents Cross-Site Tracking. Cross-Site Tracking is occurs when, "a third-party service could set a cookie when embedded on one website and then access that same cookie when embedded on a completely different website. This allowed for tracking user activity across unrelated sites." So, from CVS.com, my browser had three separate pieces of data stored on it. From here, the choices are delete the data by clicking the top trashcan icon, or delete the individual pieces of data by clicking each individual trashcan icon. | |
|
|
|
| It can be quite jarring when you look at all the various websites and/or servers that have planted data in your browser. I did not expect, but was not all that surprised either, to see that a webserver located in Russia had planted its data in my browser. Below is what I had found inside the cookies set by the common US News site, politico.com. Any website where the URL ends in ".ru" comes from Russia. And it is my opinion that nothing comes From Russia With Love. | |
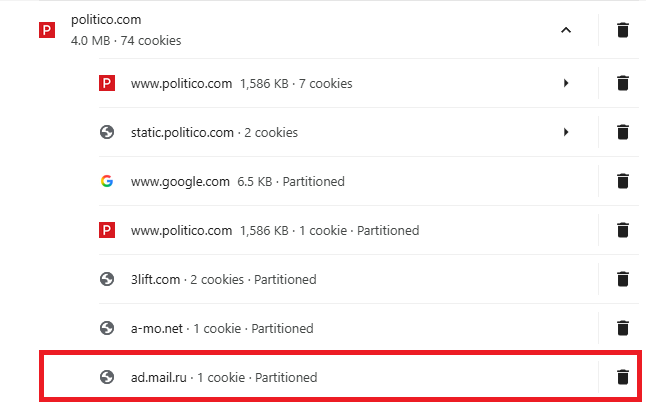 |
|
| I found other bits of site data that had emanated from Russia. The domain shown below, dmg.digitaltarget.ru, was also present in different cookies. The screenshot shows that this is not a benign marketing website. Data from web servers located in Pakistan were also found. | |
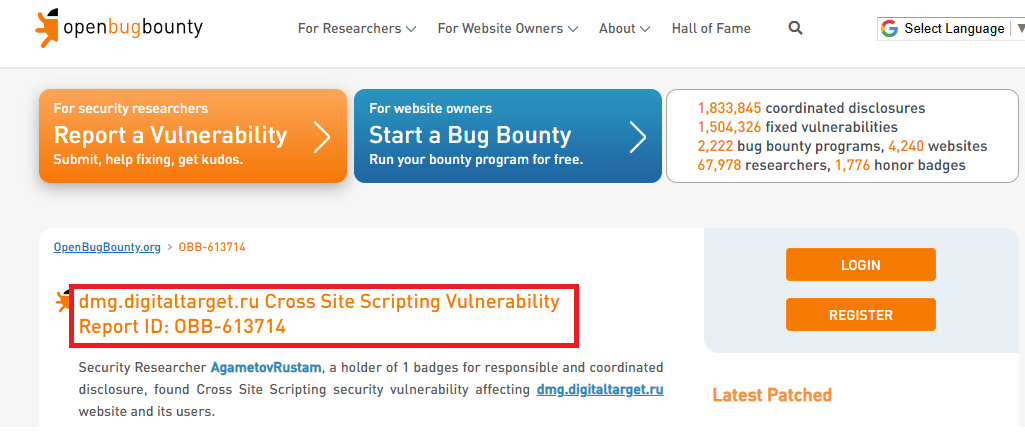 |
|
As I said at the outset, going through each cookie saved into the browser cache was tedious, to say the least. On the other hand, it was neither a waste of time; nor was doing so merely an academic exercise. The process yielded real tangible results. I got the Russkies out of my digital system, and I learned a great deal more about the nature of cookies.
As the subtitle of this article implies, what is laid out here in is in a defensive posture. The harm, if any, was already done. The steps outlined herein are meant to mitigate the effects of cookies automatically stored in the browser cache.
Of course, I now must deal with these nagging popups again.

I don't get sent anything strange like
underwear.
I get sent cookies.
— Jennifer Aniston
Gerald Reiff