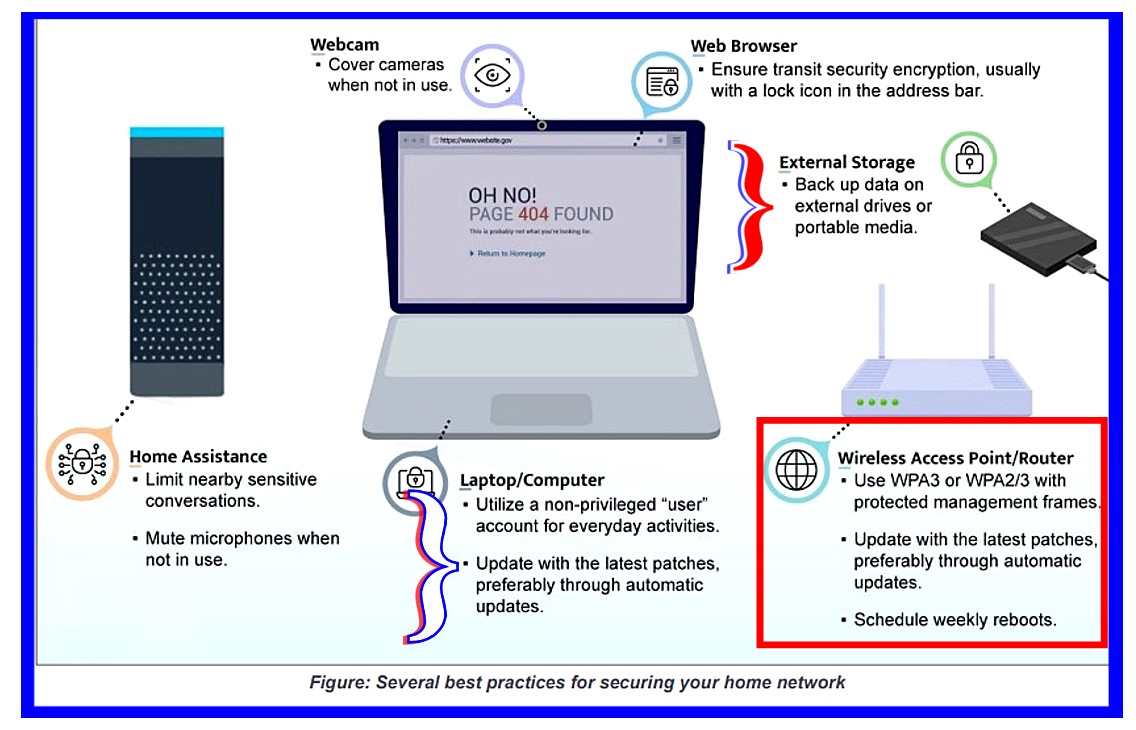
NSA Publishes Tip Sheet On How To Secure a Home Network
A
Few Words to the Wise DIYs: A View From the Ground Up
The NSA has released a Guide to
Best Practices for Securing Your Home Network.
(9pp PDF will open.) As
do many of the Cheatsheets released by Uncle Sam, its prescriptions and proscriptions will
sound familiar to Readers of The Dispatches From the Front.
Indeed, I do recommend most of these practices to my clients, but not
all of them. When taken as a whole, what these 9 pages tell the
SMB is that Dear Mr. or Ms. Small Business
Owner, you need full time professional help if you plan to implement all
of these suggested measures using the graphic above as reference.
Most SMBs do not have any budget for full time tech help. And if
they did the owner would soon come to resent the tech's salary being paid for
sitting around most of the day waiting for something to happen.
Or, the tech would be unhappy when drafted into non-IT work.
That
said, let's review, as I see them, the pros and cons of some of the more
salient issues presented discussed in the document. My paradigm
comes from that of an old road warrior out in the field probably too long,
and not that of someone thirty-something writing from a cushy air
conditioned office with all the tech help taxpayers' money can buy.
Issue 1, (pg. 2):
Upgrade to a modern operating system
and keep it up-to-date
The
most recent version of any operating system (OS) contains security
features not found in previous versions. Many of these security features
are enabled by default and help prevent common attack vectors. Increase
the difficulty for an adversary to gain privileged access by using the
latest available and supported OS for desktops, laptops, and smart
devices... Enable automatic update functionality when available. If
automatic updates are not possible, download and install patches and
updates from a trusted vendor on a monthly basis.
Updates do occasionally fail, however. If a user does as
recommendation to: "Leave computers in sleep mode to enable
downloading and installing updates automatically," and that
update fails and disables some feature or process on the system, there
would not be the immediate knowledge of cause and effect. On Feb.,
06, 2022, I posted
How to Run Windows Update Manually. I still maintain
that running updates yourself first thing each day should be routine.
The NSA and I agree that "Your router is the gateway
into your home network. Without proper security and patching, it is more
likely to be compromised, which can lead to the compromise of other
devices on the network as well. " (pg. 2) The NSA
document recommends regular rebooting of your router. (pg. 5)
Schedule frequent device reboots
To minimize the threat of non-persistent malicious code on
your personally owned device, reboot the device periodically. Malicious
implants have been reported to infect home routers without persistence.
At a minimum, you should schedule weekly reboots of your routing device,
smartphones, and computers. Regular reboots help to remove implants and
ensure security.
The sentence "Malicious implants have been reported to infect
home routers without persistence." refers to the recent
discovery that because there is no device to save the attacker to, any
malware infecting your router will be removed when powered down.
The report furthers notes the importance of updating router
firmware.
To minimize vulnerabilities and improve security, the routing devices on your home network should be updated to the latest patches, preferably through automatic updates. These devices should also be replaced when they reach end-of-life (EOL) for support. This ensures that all devices can continue to be updated and patched as vulnerabilities are discovered.
This is all well and good. I am in complete agreement. But the practicality of one person trying to run a business, and yet constantly investing the considerable time involved to ensure the networking gear has all of its updates that are available, makes the issue almost moot. Few SMBs I have known, have any idea that the router has an internal interface to log into the inner workings of their router. Moreover, many would simply be terrified to do so. Further muddling this situation is the many vendors who just do not offer clear upgrade paths to their devices. Finally, after three years of enduring this endurance course, the SMB must toss out the device and buy a new one. Networking gear is opaque to most users. Until this situation improves, this issue will remain a very weal link in the overall security stature of the entire Internet.
Employ firewall capabilities
Ensure that your personally owned routing device supports basic
firewall capabilities. Verify that it includes network address
translation (NAT) to prevent internal systems from being scanned through
the network boundary.
One issue most SMBs face, but may not know it, is your ISP doesn't give
a Horse's Patootie about their customers' security
posture. The ISPs often supply their customers outdated gear that has
little security built in, and that gear may also often conflict with third party
firewall products. The NSA Directive recommends purchasing your own
network gear (pg 2), which I am recommending clients do. The newer
DOCSIS 3.x modems are faster and more secure. But because of the
predatory pricing ISPs offer for the complete package the ISP offers,
including Voice Over IP telephone service, many people have their
telephone calls routed through the modem gateway. That is one more
layer of complexity that makes securing the network more difficult with
third party networking devices.
Furthermore, far too many SMBs and users in general, like the ISPs, just
don't care one Horse's Patoot when it comes router security.
The
Directive places much emphasis on the newer WPA3 wireless security
protocol. Also know as
Wifi 6 or 802.11ax protocol, these newer devices
have been in the field for several years. Wifi 6 throughput is
faster; the newer protocol is superior
when connected to mesh devices to expand connectivity throughout the
dwelling; 802.11ax offers better and more reliable steaming of media;
but in most standard implementations Wifi 6 is in practice
no more secure than its recent predecessor protocols.
Furthermore, all devices on the network must also employ the 802.11ax
protocol to benefit from the speed increase. In a perfect world,
we all would always have the newest and best of everything and at all
times. But until Star Trek's Replicator is in mass production and
mass distribution, we all got we got until we get something different.
And somehow we still muddle through the day.
As someone who, because
of his position as an independent IT consultant, is very cognizant of
the fact that I am to some degree or another ethically, but maybe not legally,
responsible for my clients' data remaining intact. I absolutely
support the document's assertion that they only way to backup your data,
Madame
SMB, is to a portable USB hard drive that can be removed from the system
when not in use. (pg 4)
Exercise secure user habits
To minimize ransomware risks, back up data on external drives or
portable media. Disconnect and securely store external storage when not
in use.
The crooks cannot steal or encrypt your data if that data set in not
present on ANY NETWORK. The document doesn't even contain the word
"cloud" in reference to storage. I do, however, differ with the
NSA on disk encryption. I have been associated with the
electronics industry in one form or another since 1975, and specifically
computers since 1985. Machines
break; software becomes corrupted and crashes; power failures can have
devastating effects on computer gear. These are just some of the
everyday occurrences that can wreak havoc on devices and/or software.
Moreover, users now cannot easily manage passwords to websites; but at
least those passwords can be easily changed. Forget your encryption key
password and it's just about game over for the SMB. I will not be
the party responsible for that kind of cyber wreckage. If a user
wants to implement full drive encryption that is their choice; and is
mine not to participate.
The document does mention
password management.(pg.4) Here it seems a bit behind the curve.
Indeed, "Passwords should be strong, unique for each account, and
difficult to guess." But the authors of this NSA guide seem to be completely unaware of
all the nightmares caused users by their favorite password manager
having been hacked very recently.
Norton Lifelock was hacked in late 2022.
Users of LastPass were notified by the vendor that each users'
"vault" were compromised resulting in the likelihood of ALL USERS
passwords for all accounts stolen. I don't really
have an answer to the ever worsening password conundrum, other than
write them down in a logical manner, sorted alphabetically, and then
that is stored in a safe manner.
Amazon offers an absolutely marvelous analogue Password Manager
for a ridiculously low price of $13.99!
Hacker Proof,
Guaranteed. But NOT All Crooks Proof. Put it somewhere safe.

source:
https://www.amazon.com/Boxclever-Press-Password-Alphabetical-usernames/dp/B087D36YF8?ref_=ast_sto_dp
Ain't it a thing of beauty? You Betcha!
As has been true in all times of rapid change that have come before, navigating through life has always entailed evaluating and
managing risks. And so it is with even the most secure computer
installation. We all do what it is we can do. Prepare for
the next step along the journey. And evaluate where we have been so
as to have a better idea about where to go next. This NSA document
is an excellent roadmap to more secure computing. And allows users
to benchmark their own security posture and prepare for the next steps.
It is worthwhile to
download the PDF and evaluate your own security
posture.
I have one primary goal in providing support to computer users.
And this goal is to avoid fielding the phone calls that comes after what is conveyed in
the image below. Prevention is always preferable to intervention.

source DALL-E
Prompt: colorful
graphic showing a frantic woman with red hair and green eyes staring at
virus infected computer
Woke up this morning,
I was feeling
quite weird
Had flies in my beard, my toothpaste was
smeared
Over my window, they'd written my name
Said, "So long, we'll see you again"
— Mr. Spaceman,
Roger McGuinn, (The Byrds)