

Stupid Is As Stupid Does:
ClickFix Continues to Exploit
Users' Naïveté

On
June 20, 2024,
The Dispatches posted a two part series about how
users were being duped into infecting their computers by tricking naive
users by first opening a Command Prompt. Then, once the
Command window was open, the victims of this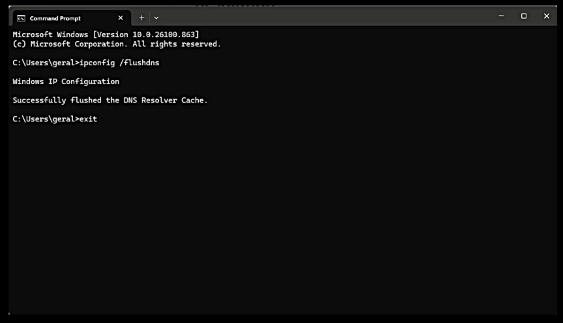 exploit were further duped
into copying and pasting malicious code into the Command window. At that time, fake prompts to update
not just
Google Chrome, but fake prompts to update
Microsoft Office and Microsoft OneDrive were also
used to trick unsuspecting users into infecting their machines. Of
course, there are no circumstances where a PowerShell or Command window
needs to be opened to update the apps mentioned. So, as a
counterpoint, I offered instructions on how to legitimately update
Chrome and Office from within those respective apps.
exploit were further duped
into copying and pasting malicious code into the Command window. At that time, fake prompts to update
not just
Google Chrome, but fake prompts to update
Microsoft Office and Microsoft OneDrive were also
used to trick unsuspecting users into infecting their machines. Of
course, there are no circumstances where a PowerShell or Command window
needs to be opened to update the apps mentioned. So, as a
counterpoint, I offered instructions on how to legitimately update
Chrome and Office from within those respective apps.
I was incredulous that this method of exploit would be successful. I was skeptical that any user would blindly open a window that they had probably never seen before, and then copy and paste a string of text into an application without any forethought. In the original posting, I explained that there are a few reasons for a typical Consumer to use PowerShell or open a Command window. For instance, referencing a page from Microsoft.com, I offered a short tutorial on how to use Command Prompt to flush the DNS cache. I used the example to show that a Command window or PowerShell window are useful but seldom used features of Windows, at least by most Consumers. Thus, any out of the blue prompt to open either of these apps was a form of attack. Seemed clear, uh?
Well, I was wrong. The past several weeks have brought more
reports about what is called a ClickFix attack.
BleepingComputer reported, November 24, 2025, that
a new ClickFix attack is in the wild. The article's title told the
tale very well, "ClickFix attack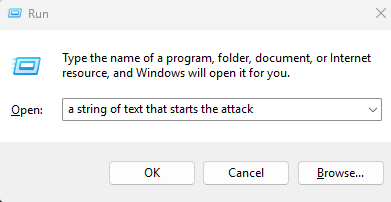 uses fake Windows Update screen to push malware." In this
current iteration of what should be by now be a well known attack, bogus Windows Update
screens pop up, telling the user that in order to complete the update,
the user must do what's listed below. The difference with this
attack is that the user is simply prompted to open a Run Dialog Box.
No PowerShell needed. Then a JavaScript will automatically copy
the attack string into the Run Dialog Box.
uses fake Windows Update screen to push malware." In this
current iteration of what should be by now be a well known attack, bogus Windows Update
screens pop up, telling the user that in order to complete the update,
the user must do what's listed below. The difference with this
attack is that the user is simply prompted to open a Run Dialog Box.
No PowerShell needed. Then a JavaScript will automatically copy
the attack string into the Run Dialog Box.
Step 1 — Hold "Windows Key" Press
"R" (To open a Run Dialog Box)
Step 2 — Hold "Ctrl" Press
"V" (To Paste)
Step 3 — Press "OK" or "Enter"
This same attack might also employ a fake human verification page, a form of CAPTCHA. In both cases, the malicious code is embedded into the image files that make up the screen visuals. The CAPTCHA has become a common attack vector for ClickFix exploitation.
Microsoft has published an in-depth discussion of ClickFix attacks. The article titled might have been inspired by my Uncle Sam graphic below, which I have used off and on since May 2023. "Think before you Click(Fix): Analyzing the ClickFix social engineering technique," gives a detailed overview of the history of the different types of ClickFix attacks. The authors describe how almost every known form of attack from bogus email links to fraudulent Google ads have been used and abused by the ClickFix methodology to infect computers and steal people's valuable information or worse.
TikTok videos have also gotten into this quite awful act. A report of October 19, 2025, also by BleepingComputer, discusses how fake instructional videos have been used to steal users' information. The article titled, "TikTok videos continue to push infostealers in ClickFix attacks," explains that in videos that purport to explain how to activate common applications like Microsoft Windows, Office 365, and various products by Adobe, users are duped into opening a PowerShell window and post a one line script into PowerShell. In its article, author Lawrence Abrams frankly advises any reader who was so duped by the exploit that: "Users who perform these steps should consider all of their credentials compromised and immediately reset their passwords on all sites they visit." Read 'em and weep, as the saying goes.
And, just when you thought it was safe to boot up the macOS device, ClickFix attacks are now being staged against Apple Computer products. The Hackers News reported, June 06, 2025, on a campaign targeting not only Windows machines, but Apple macOS systems are attacked with the same ClickFix modus operandi. Here typosquatting is used to lure users to bogus websites with URLs similar to, but not exactly the same as, the legitimate sites the cybercrooks are emulating. One such company impersonated in this attack was the cable and Internet provider, Spectrum. When users landed on the fake website, a fake CAPTCHA was displayed. When that human verification method would ultimately fail, an alternative verification method was offered. The alternative verification required the opening of the terminal app on the now compromised Apple machine. The user was then prompted to input their Apple account credentials.
In another ClickFix attack targeting Apple users, fake Facebook ads are used to lure users to a bogus TradingView site. As reported by security vendor Moonlock, November 21, 2025, in an article titled, "ClickFix malware is infecting Macs via Facebook ads for fake AI apps," author Ray Fernandez discusses how once a user lands on the bogus trading site, a fake “download for macOS” button begins a file download, and sends the targeted device a series of instructions to follow. Following the instructions will run a series of scripts that will compromise the Apple device. This attack, dubbed MacSync, is reported to have been "deployed in Europe and North America, as well as in Morocco, Ukraine, Brazil, Argentina, Japan, India, Australia, and many other countries," reports author Fernandez.
One has to wonder about the gullibility of otherwise well-heeled computer users. Apple computers are not cheap compared to generic PCs. Apple customers must have some level of sophistication and savvy. When I first wrote about ClickFix attacks in June 2024, I thought this can't last. People will catch on. Well, all I can say is Mea Cupla and:

The important take away, however, is always follow the advice of Uncle Sam (and Microsoft) below.

Gerald Reiff
| Back to Top | ← previous post | next post → |
| If you find this article of value, please help keep the blog going by making a contribution at GoFundMe or Paypal | ||