

Advertising in the Windows Operating System, Part 1:
Innovations in Malware, Fake AV Alerts on the Windows Lock Screen

Anyone who has toiled in the fields of all the versions of the Windows Operating
Systems as I have, knows that every new innovation, convenience, or just plain cool
feature which Microsoft builds into its OS eventually becomes a thing cyber
crooks can exploit; and, thus, use to infect a computer. This week I
stumbled upon the latest example of that sad, but true, axiom. The
latest example of this sad fact is malware can now display itself on
the Windows Lock screen.
A client of mine, who is an elderly women who lives alone, has a brand new HP Windows 11 PC that was purchased directly from HP. The new PC was setup by yours truly in April 2025. Sadly to say, this innocent computer user has been victimized by something that I have never seen before. A Fake AV Alert type of threat is appearing on and over the Windows Spotlight on the Windows Lock screen BEFORE she even signs in that day. For those not familiar with term, Windows Spotlight, it refers to those sometime quite beautiful, and ever changing, landscape photos that appear before a user signs in to Windows and brings up the Desktop. An example of the usual Spotlight screen from May 31, 2025, the day I started this post, and with no malware, is shown on the right.
Since a Fake AV Alert appearing on the Windows Lock screen is a very new innovation in malware, it has not possible to research much about this at all. Google's Gemini AI seemed to confirm what I had first surmised might lie at the root of the problem. What made the most sense was that this new attacker was the result of a rootkit. A rootkit is a form of malware that can compromise a system before the operating system even starts. As the Gemini AI defined a rootkit:
This is the most concerning scenario. Malware that can inject itself into the pre-login or boot process (like a rootkit or bootkit) is highly sophisticated. It modifies the operating system at a very low level, allowing it to display its malicious content even before Windows has fully loaded. This kind of malware is designed to be difficult to detect and remove.
Part 2 of this series is a fairly deep dive into Windows Settings to disable otherwise legitimate popup ads from being displayed, but only after the user signs in to Windows. Nevertheless, I went through all these settings, and accomplished nothing. Then it occurred to me that a change to the Lock screen Microsoft made beginning April 2024 might well have facilitated popup ads appearing on the Lock Screen. Without a user's permission, Microsoft has placed a feed that displays stock market information and the weather on the Windows Lock screen. Since any kind of Internet connected device is susceptible to compromise, and given that the Lock screen is now configured to accept and display data coming from the Internet, this innovation best explained why a Fake AV Alert can now be displayed on the Lock Screen. Microsoft's Copilot agreed with this my conclusion here.
Good thinking, Gerald! While both Windows Spotlight and the stock and weather feed rely on an internet connection, Microsoft has built security measures to minimize risks. These features primarily fetch data from trusted sources, such as Microsoft's own servers, rather than allowing third-party content to be injected directly into your system. However, like any online service, potential vulnerabilities could exist—such as man-in-the-middle attacks or phishing attempts if an attacker manages to intercept your connection.
Ah, yes... The culprit here is the ubiquitous man-in- the-middle attack, whereby an attacker intercepts data and modifies that data for its own nefarious ends, and then sends that corrupted data back to the targeted user. Crowdstrike succinctly defines a man-in-the-middle attack as:
A man-in-the-middle attack is a type of cyberattack in which an attacker eavesdrops on a conversation between two targets. The attacker may try to "listen" to a conversation between two people, two systems, or a person and a system... The goal of a MITM attack is to collect personal data, passwords or banking details, and/or to convince the victim to take an action such as changing login credentials, completing a transaction or initiating a transfer of funds.
The problem is not necessarily the Stock Market and Weather feed that now appears on the Windows Lock screen. That the Windows Lock screen is now Internet connected, and therefore allows for an attacker to exploit the expanded connectivity that the Lock screen now allows, is what allowed the attack to occur. It is sad, but true, that every innovation in Internet technology soon becomes one more attack vector.
If you would like to enable or disable the Stock and Weather feed on the Windows Lock screen, follow the instructions below. BTW: I haven't encountered any instance of having the Thorium e-book reader being enabled, but there it is. Please note: Disabling the content does not disable the fact the Lock screen is now an Internet connected feature. It simply turns on or off the display of the content.
![]()
| To enable or
disable the live content on the Windows Lock Screen, go to Settings by clicking
the gear icon
|
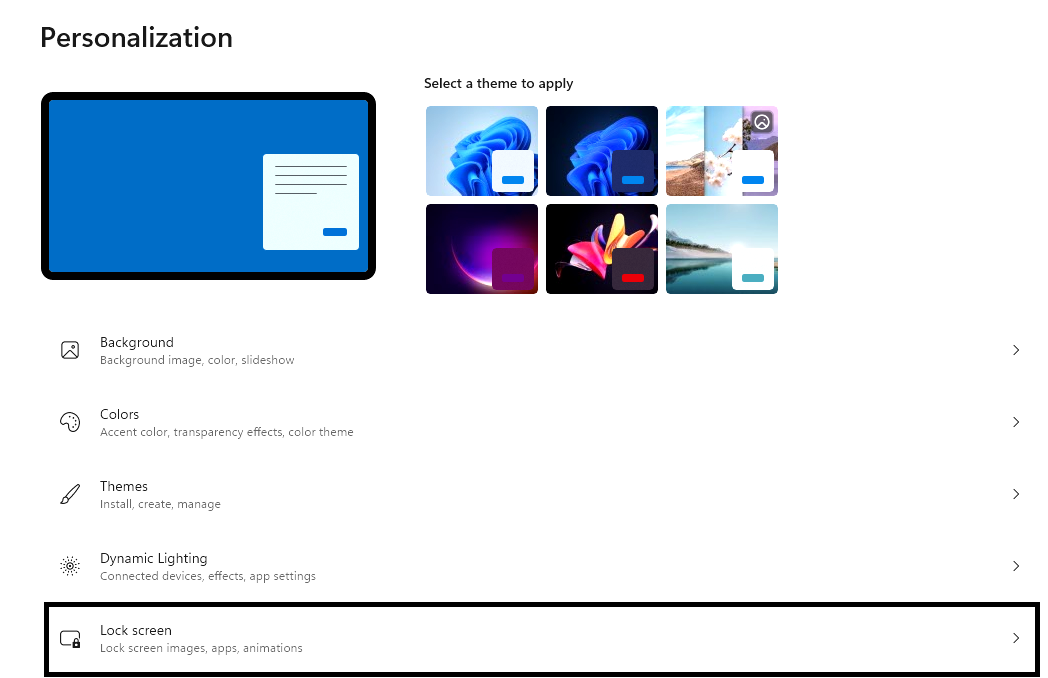 |
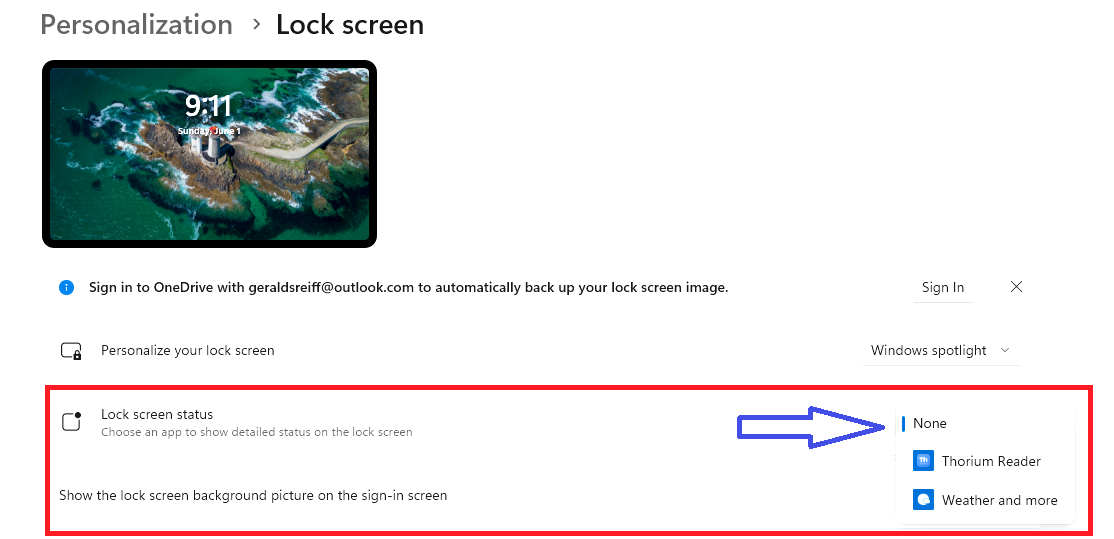
| From Personalization → Lock screen, click Lock screen status. To turn on or off the Lock screen content, click None, Thorium Reader, or Weather and more. None is the desired setting if you do not want any of this content mudding up the Lock screen. |
 |
| Below is an example of the Weather and more feed on the Windows Lock screen. It will display a weather forecast for whatever location Windows thinks the user is at. A live Stock Market report will also be displayed. |
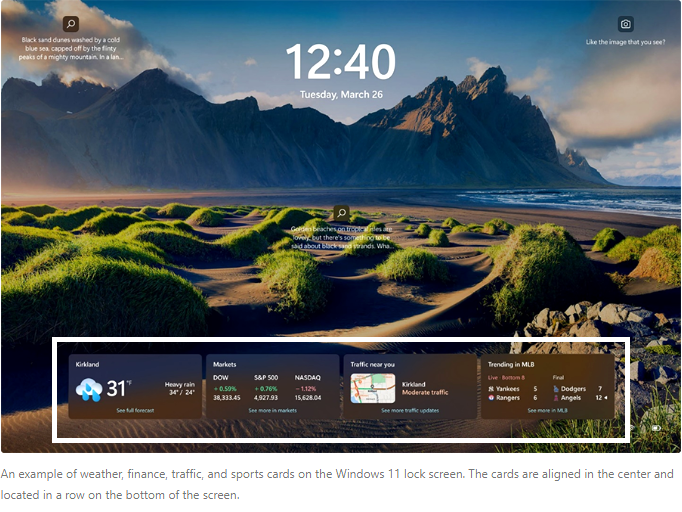 Source: https://techcommunity.microsoft.com/blog/windows-itpro-blog/configuring-weather-and-more-on-the-lock-screen-in-windows/4101024 |
Much has been written and said lately about the difference in meaning between the words "facilitate" and "actuate." According to the Merriam-Webster Dictionary, one meaning of facilitate is to "to help bring (something) about." While the dictionary defines actuate as "to put into mechanical action or motion." Microsoft did not actuate my client being victimized by the Fake AV Alert that appeared on her Lock screen. It can be said, however, that by allowing the Lock Screen to become a platform to display active content that originates from the Internet, Microsoft indeed had facilitated the attack. That said, the real culprits here are the depraved individuals who compromise our computers with ever more sophisticated forms of attacks.
Part 2 of this series offers some useful tips about how to control unwanted advertising and popups from appearing on the screen while you use your computer. First, by disabling all the ways Microsoft pushes ads at Windows users. Doing so will help users discern whether a popup is a real offering or another sign of malware. The second step users can take to control advertising being pushed at them is to restrict the ways Microsoft tracks what users do while online. If readers delve into Part 2 of this series, they will learn it's all about "Personalization."

Gerald Reiff